Domain Name System Security Extensions (DNSSEC) are a set of extensions for DNS. DNSSEC allows the client to cryptographically check that DNS data, including the IP addresses of domains, are authentic. This eliminates a number of security threats, including spoofing attacks, by which an attacker can generate a forged DNS response with an incorrect IP address, making it possible to forward the client to a server that is controlled by the attacker.
Client operating systems, including Windows 10, do not support DNSSEC and cannot validate DNSSEC themselves. They can only work together with a trusted DNS server that fully supports DNSSEC.
Basically, such systems simply delegate DNSSEC support to the server. This is called a security-aware client or AD-bit-aware stub resolver.
Windows Server supports DNSSEC beginning with Windows Server 2012. Unfortunately, Windows Server provides DNSSEC support only when it acts as the DNS server. The DNS client of Windows Server still cannot validate DNSSEC by itself.
To make the Windows client DNSSEC aware, one can use the Name Resolution Policy Table (NRPT) that is available through the Local Group Policy Editor (gpedit.msc).
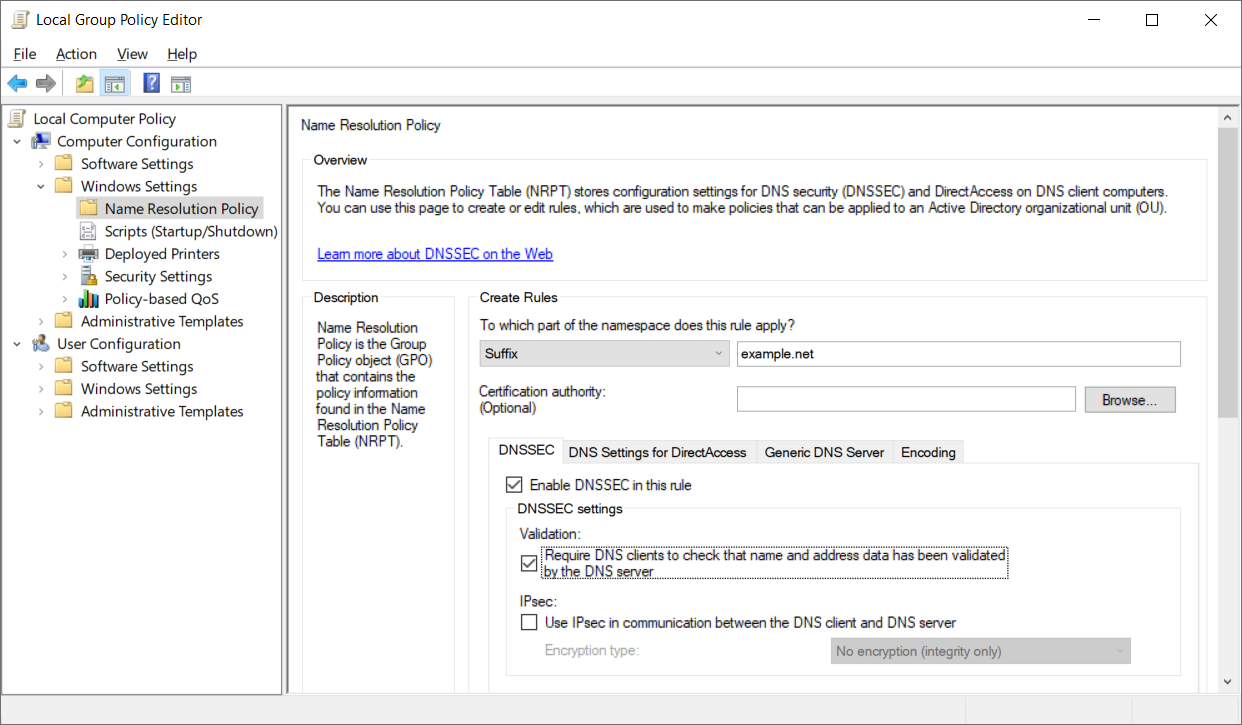 Name Resolution Policy Table with DNSSEC enabled for the example.net domain
Name Resolution Policy Table with DNSSEC enabled for the example.net domain
At the technical level, all security is based on the Authenticated Data (AD) bit of the DNS protocol. The DNS server sets this bit if the data were properly validated with DNSSEC. Windows resolver itself does not validate the DNSSEC signatures. It completely depends on the AD bit of the DNS packet that travels over the network from the server. This approach can work only if the DNS server with DNSSEC support is trusted and if the connection to this server is secure. If a DNS server is located in a public network, the concept of a "security-aware" DNS client becomes useless. An attacker can easily forge or change DNS data, including IP addresses.
Unlike the Windows system resolver, YogaDNS fully supports DNSSEC. It can validate all DNSSEC signatures locally. This ensures that DNS data, including domain IP addresses, are authentic. YogaDNS works transparently for the applications and automatically intercepts the requests of the system resolver. Thus, you can quickly and easily make your system work with DNSSEC.
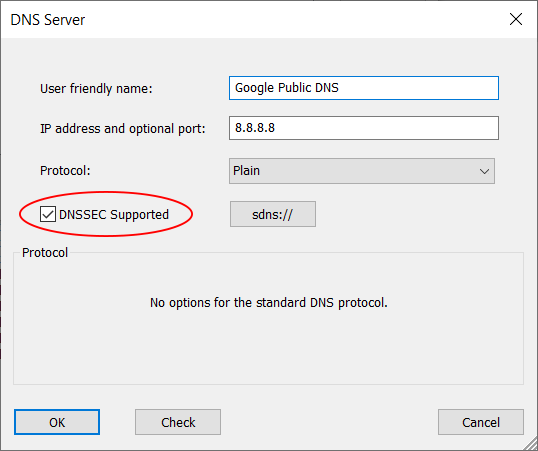 Google Public DNS with DNSSEC support
Google Public DNS with DNSSEC support
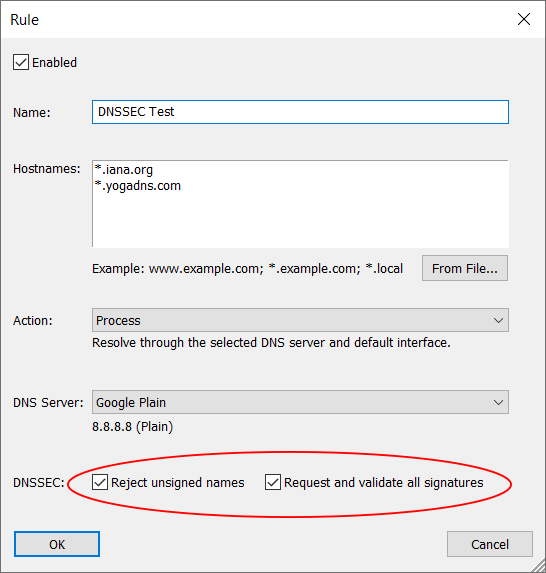 Example of the DNSSEC test rule for hostnames *.iana.org and *.yogadns.com
Example of the DNSSEC test rule for hostnames *.iana.org and *.yogadns.com
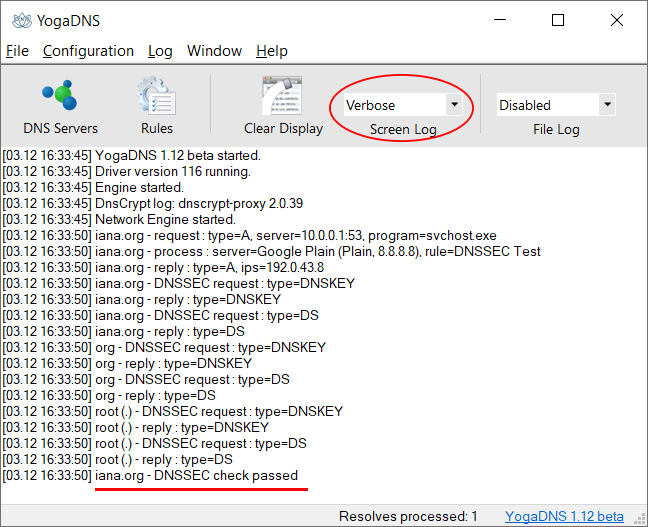 Validation example for iana.org DNSSEC
Validation example for iana.org DNSSEC
It is important to note that DNSSEC is not yet enabled for many domains. Thus, you may wish to enable DNSSEC validation for only the limited set of domains that already support it.
You can get even more security if you use encrypted DNS protocols, such as DNSCrypt or DNS over HTTPS. YogaDNS can work with DNSSEC over these protocols.
In verbose output, you can see that YogaDNS recursively checks all DNSSEC signatures up to the root (.) for every requested hostname. This is the most secure way for a DNS client to validate the authenticity of DNS data with DNSSEC.
[03.12 16:33:50] iana.org - request : type=A, server=10.0.0.1:53, program=svchost.exe [03.12 16:33:50] iana.org - process : server=Google Plain (Plain, 8.8.8.8), rule=DNSSEC Test [03.12 16:33:50] iana.org - reply : type=A, ips=192.0.43.8 [03.12 16:33:50] iana.org - DNSSEC request : type=DNSKEY [03.12 16:33:50] iana.org - reply : type=DNSKEY [03.12 16:33:50] iana.org - DNSSEC request : type=DS [03.12 16:33:50] iana.org - reply : type=DS [03.12 16:33:50] org - DNSSEC request : type=DNSKEY [03.12 16:33:50] org - reply : type=DNSKEY [03.12 16:33:50] org - DNSSEC request : type=DS [03.12 16:33:50] org - reply : type=DS [03.12 16:33:50] root (.) - DNSSEC request : type=DNSKEY [03.12 16:33:50] root (.) - reply : type=DNSKEY [03.12 16:33:50] root (.) - DNSSEC request : type=DS [03.12 16:33:50] root (.) - reply : type=DS [03.12 16:33:50] iana.org - DNSSEC check passed
YogaDNS caches the signatures of all subdomains during the resolution. This allows the faster processing of future validations because many domains have common parts (e.g., ".com"). Set the
If a domain has no DNSSEC signature, YogaDNS detects this and, depending on its settings, can block this request. This prevents client applications from receiving untrusted data.
[03.12 16:53:12] wikipedia.org - request : type=A, server=10.0.0.1:53, program=svchost.exe
[03.12 16:53:12] wikipedia.org - process : server=Google Plain (Plain, 8.8.8.8), rule=DNSSEC Test
[03.12 16:53:12] wikipedia.org - reply : type=A, ips=91.198.174.192
[03.12 16:53:12] wikipedia.org - DNSSEC check failed (answer is not signed)
The same happens if any DNSSEC signature in the chain is invalid:
[03.12 17:12:38] sigfail.verteiltesysteme.net - request : type=A, id=2110, server=10.0.0.1:53, program=svchost.exe, pid=1204
[03.12 17:12:38] sigfail.verteiltesysteme.net - process : server=Google Plain (Plain, 8.8.8.8), rule=DNSSEC Test
[03.12 17:12:38] sigfail.verteiltesysteme.net - reply : type=A, id=1, ips=134.91.78.139
[03.12 17:12:38] verteiltesysteme.net - DNSSEC request : type=DNSKEY, id=59910
[03.12 17:12:38] verteiltesysteme.net - reply : type=DNSKEY, id=2
[03.12 17:12:38] verteiltesysteme.net - DNSSEC request : type=DS, id=27445
[03.12 17:12:38] verteiltesysteme.net - reply : type=DS, id=3
[03.12 17:12:38] net - DNSSEC request : type=DNSKEY, id=58652
[03.12 17:12:38] net - reply : type=DNSKEY, id=4
[03.12 17:12:38] net - DNSSEC request : type=DS, id=35507
[03.12 17:12:38] net - reply : type=DS, id=5
[03.12 17:12:38] root (.) - DNSSEC request : type=DNSKEY, id=9021
[03.12 17:12:38] root (.) - reply : type=DNSKEY, id=6
[03.12 17:12:38] root (.) - DNSSEC request : type=DS, id=20584
[03.12 17:12:38] root (.) - reply : type=DS, id=7
[03.12 17:12:39] sigfail.verteiltesysteme.net - DNSSEC check failed
The tests confirm that YogaDNS can successfully enforce the security of name resolution with DNSSEC.